|
APCO 2P11 Lab 9
|
|
Objective
In this lab you will focus on learning the roll the windows registry
plays. You will look at the components of the registry and learn how
to manually edit it.
Introduction & Startup (5 min)
Set up your Dell machines and boot into windows.
Exercise 1 (25 Min)
The windows registry is a database used by windows to hold
configuration settings from everything to an installed application
down to individual user preferences. Rather then repeat what has
already been written, go to wikipedia [http://en.wikipedia.org/wiki/Windows_registry]
and
read up on the registry. Don't do any modifications yet, that will
come. When you are finished reading, answer the following questions.
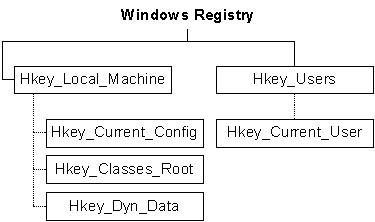
What is the windows registry?
What is a key?
What are the 5 main registry classes and their associated
abbreviation?
What tool do you use to gain access to the registry?
Exercise 2 (30 Min) (Registry Backup)
Playing around with the registry can cause severe problems to arise
if you are not careful. It is important to learn how to back up the
registry or system state prior to making any changes. At worst, if
things don't work out, you can restore the previous version. There
are a variety of ways to say the system state. Let us go through a
few.
Backing up the Win 7 Registry
Method 1: Using System Restore
One way to backup the registry is to
create a System Restore snapshot. System Restore returns your
computer to a previous snapshot without losing recent personal
information, such as documents, history lists, favourites, or
e-mail. It monitors the computer and many applications for changes
and creates restore points. You restore these snapshots when your
configuration isn't working. This method is unreliable in case you
want to rollback the registry changes made a longtime ago, in
which case the System Restore might have purged that particular
restore point - due to space constraints or due to a recent system
restore point or even a Restore point corruption. Please remember,
System Restore points get deleted for many reasons, making it
unreliable, especially in the long run.
How do I create a System Restore point?
Click Start, right click Computer -> properties
On the left, select System Protection
At the bottom is a button Create...
1) Try
creating a system restore point.
Method 2: Backing up the selected branch of the registry by
exporting (Reliable)
This method is preferred if you're making changes to a specific
key/area of the registry. To backup a selected branch/key in the
registry, try this:
- Click Start, and then type regedit.
- Locate and then click the key that contains the value that you
want to edit
- On the File menu, click Export.
- In the Save in box, select a location where you want
to save the Registration Entries (.reg)
- In the File name box, type a file name, and then click Save.
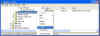
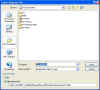
(Backing up a selected branch/key of the registry)
Now that you've created a Registry backup for that particular
key. Save the REG file in a safer location in case you want to
undo the registry changes made. You can restore the settings by
just double-clicking the REG file. It automatically merges the
contents to the Registry.
-
Registration
Files:
The Registration Files option creates a .reg file. This is
probably the most well known file format used for backing up
the registry. The Registration File can be used in two ways.
As a text file it can be read and edited using Notepad
outside of Registry Editor. Once the changes have been made
and saved, right clicking the file and using the [Merge]
command adds the changed file back into the registry. If you
make additions to the registry using regedit
and then merge the previously saved Registration File,
anything that you've added via regedit will
not be removed, but changes you make to data using regedit
that previously existed in the saved Registration File will
be overwritten when it is merged.
-
Registry
Hive Files: Unlike the Registration Files option above, the
Registry Hive Files option creates a binary image of the
selected registry key. The image file is not editable via
Notepad nor can you view its contents using a text editor.
However, what the Registry Hive Files format does is
create an image perfect view of the selected key and allow
you to import it back into the registry to ensure any
problematic changes you made are eliminated.
2) Open regedit. Using the
above method make a backup copy of the following key. Save the
backup somewhere safe, for the purpose of the exercise put it in
the windows temp directory. Call the file desktop.
HKEY_CURRENT_USER\Control Panel\Desktop
What benefit does a hive
file have over a reg file?
For practice, create a hive file of the above key.
Method 2 (a) : Export registry keys using a command-line
(Console Registry Tool)
You can use the Console Registry Tool for Windows (Reg.exe) to
edit the registry. For help with the Reg.exe tool, type reg
/? at the Command Prompt.
4) Open a command window,
see accessories, cmd.
type reg /?, one of the options is to query a specific
registry key.
Try to query
HKEY_CURRENT_USER\Control Panel\Desktop, note: if the key has any
spaces in it, like this one does, you will need to enclose the
entire key in double quotes "".
Example: To export the key [
HKEY_CURRENT_USER\Control Panel\Desktop] and it's sub-keys, try
this from Command Prompt:
REG EXPORT "HKEY_CURRENT_USER\Control
Panel\Desktop" C:\desk.REG
To view the REG contents type notepad C:\desk.reg in
Start, Run dialog. Console Registry Tool is extremely handy for
network admins and also for home users.
Method 3: Backing up the whole registry ("System state")
For backing up the whole registry, use the NTBackup utility to
back up the System State. The System State includes the registry,
the COM+ Class Registration Database, and your boot files. See
section "Back Up the Whole Registry" in the following article:
We won't be doing this. Instead lets take a look at some third
party software. From the
APCO 2P11 software folder , install Erunt. It will say for
XP and NT but works fine with win7.
After you install and run
the software, goto the Windows/Erdnt directory. Notice that the
backup includes all parts of the registry, including an
NTuser.dat for each user login on the machine. These are exact
images of the registry files. Should things go bad, then a
restore will put set the registry back to the saved state.
Exercise 3 (30 min.) (Lets Play!)
As you might of guessed by now, Windows has a registry editor called
RegEdit. In fact there are many such editing tools available, mostly
third party. For our purposes, we will use RegEdit. You can start
RegEdit from Start - Run.
When you have made a change to the registry, the effects may not be
immediate. In cases where a user key is changed, you must log out
and in again for the effect to be realized. When making changes to
the local machine or system keys, a reboot may be required.
There are many hacks which you can use. Google "registry, blah blah
blah", each of the following. In most cases microsoft will supply
the required information.
- Disable the Windows Key
- Hide the Internet Explorer Icon If the icon is disabled, then
enable it.
- Change the Menu Show Delay
Show your lab instructor after each registry hack.
Exercise 4 (20 min.)
Ever wonder why all those system try icons start every time you
start windows. Or why that application always starts when you log
in. The windows registry has a verity of keys which will run
applications on startup and log in. In most cases you want these to
run, for example antivirus software should start, where as some
malware like spyware will start applications and run in the back
ground doing what they are best at, spying. The result of a rather
nasty piece of malware prompted me to discover HiJackThis. This
application scans the registry for any keys which instruct programs
to start executing on startup. These keys may come from system
files, registry or startup files. Download HiJackThis from the
resource section.
For a complete list of Hjt entries refer to [http://www.malwarehelp.org/understanding-and-interpreting-hjt1.html].
This
is quite useful when determining why your machine is doing funky
things. Caution:
Hjt
will list all programs which run on startup. Some of these are
required for your machine to run smoothly. Do not arbitrarily
delete entries until you verify what they do.
- R1 – Internet Explorer Start
page/search page/search bar/search assistant URL
- R2 – This is not used
- R3 – Default URL Searchhook
- F0 – Autoloading programs
from system.ini file
- F1 – Autoloading programs
from win.ini file
- F2 } F2/F3 are essentially
F0/F1 items, mapped to the Registry.
- F3 } Only present in NT based
systems.
- N1 – Netscape 4x default
homepage and search page URLs
- N2 – Netscape 6x default
homepage and search page URLs
- N3 – Netscape 7x default
homepage and search page URLs
- N4 – Mozilla default homepage
and search page URLs
- O1 – Hosts file redirection
- O2 – Browser Helper Objects
- O3 – Internet Explorer
toolbars
- O4 – Autoloading programs
from Registry
- O5 – IE Options icon not
visible in Control Panel
- O6 – IE Options access
restricted by Administrator
- O7 – Regedit access
restricted by Administrator
- O8 – Extra items in IE
right-click menu
- O9 – Extra buttons on main IE
button toolbar, or extra items in IE 'Tools' menu
- O10 – Winsock hijacker
- O11 – Extra group in IE
'Advanced Options' window
- O12 – IE plugins
- O13 – IE DefaultPrefix hijack
- O14 – 'Reset Web Settings'
hijack
- O15 – Unwanted site in
Trusted Zone
- O16 – ActiveX Objects (aka
Downloaded Program Files)
- O17 – Lop.com domain
hijackers
- O18 – Extra protocols and
protocol hijackers
- O19 – User style sheet hijack
- O20 – AppInit_DLLs Registry
value autorun
- O21 –
ShellServiceObjectDelayLoad Registry key autorun
- O22 – SharedTaskScheduler
Registry key autorun
- O23 – Windows NT Services
Some of the more useful keys are F0, F1 and O4, These are often
attacked by Malware.
Run HiJackThis (Hjt). What programs are listed as startup
items from F0, F1 and O4.
Something which will do much the same thing is msconfig. Type this
in on Start - Run. Notice the registry keys which are listed. Select
only of these programs, and do a search using regedit to locate the
key. Do not delete it.
Open msconfig, are the same programs listed in startup? They likely
are.
Exercise 5 (20 min) Events and Services
From Control Panel - Administrative tools, start the services
console.
Windows services are (daemon) programs which run in the background
and provide a necessary service. Some of these are started when the
OS comes to life at startup. For example, locate the "Automatic
Updates" service. This service allows your computer to automatically
download Windows Updates and apply them. Can you disable this service?
You can temporarily stop this service, do so--- then re-enable it.
Note that if a service fails, you can specify options to restart the
service, what options are
these?
If anything on the machine fails or a significant event has taken
place, it is recorded in the event log. You can access the event log
by using event view. The event viewer can be accessed from
Administrative tool. What are
the 3 main classes of events? Describe what each is for.
Now lets see what was stopped and started again. The automatic
updates would be a system event. What time was the service disabled?
What time was it enabled?
Who was the last person to log into this machine and when?
Which events are recorded, are determined by the user and system
security policies. These can be changed by editing the "Local
Computer Policy". For example, to determine who has had success or
failure logging into your machine, you would turn on the Audit logon
events (provided they are not already enabled). The policy editor is
accessible from administrative tools. You will want to edit the
Local Policies and navigate to Audit Policy, turn on Audit account
log in events to monitor failures.
Exercise 6 (15 min) (Registry Cleaning)
Why should I clean my registry? [http://onecare.live.com/site/en-us/article/registry_cleaner_why.htm]
Over time, the Windows Registry can begin to contain information
that's no longer valid. Maybe you uninstalled an application
without using the Add or Remove Programs function in the Control
Panel, or perhaps an object or file in the registry got moved.
Eventually this orphaned or misplaced information accumulates and
begins to clog your registry, potentially slowing down your PC and
causing error messages and system crashes. You might also notice
that your PC's startup process is slower than it used to be.
Cleaning your registry is the easiest way to help avoid these
common problems.
Install Eusing Registry Cleaner from the resource folder. Run this
software. It should identify a number of keys which have become
outdated. It is important to not just trust that software such as
Eusing will delete all the right things. Before doing any registry
cleaning, ensure you saved a restore point or have backed up the
registry. Also, review any deletions which the software recommends.
Exercise 7 ( 15 min) (BSODs)
BSOD or Blue Screen of Death is a typical response when hardware
goes bad or a driver becomes corrupt/missing/ or outdated. Once a
BSOD happens when windows is running, a mini-dump file is created to
help diagnose the problem. These dump files can be accessed by some
third party software.
To start, lets cause windows to crash. Start the task manager
Ctrl+Alt+Del, and "Show processes from all users". Locate a process
called csrss.exe. There may be 2 of them, kill the larger of the 2.
Windows will crash!!!!!! Restart Windows.
From the resource folder, install Blue Screen
View. Start the application and inspect the latest crash.
The dump in this case may not directly implicate the cause, but it
does give a good starting point. You may find other dump files
present depending how many times you have crashed your machine.

